Cybersecurity threats are constantly growing in number and sophistication. Cybercrime is costing organizations and individuals billions every year, with global losses projected to reach trillions in the coming years. High-profile data breaches, ransomware attacks, and scams make headlines regularly, underscoring that no one is immune.
This looming threat makes it vital that IT staff understand the most common threats in information technology. This guide covers the top-most dangerous and common cyber threats, and even if you are a beginner in this field, by the end of this article, you will be better prepared to recognize these cyber attacks.
Key Takeaways
- Most cyber attacks (75%) start with phishing or mistakes.
- Ransomware encrypts files and demands payment, and it is the fastest-growing cybercrime in the world.
- Multi-factor Authentication can reduce account compromises by 99%.
- Always verify unexpected requests independently before taking action due to the rise of AI threats like DeepFakes.
16 Cyber Attacks Every Tech Team Must Know
12 Common Cybersecurity Threats in IT
Much like ice cream, cyber threats come in many flavors, but these ones are really awful, and as an IT professional, you must be aware of these:
1. Phishing Attack
Phishing is a deceptive attack where scammers impersonate legitimate entities (via email, text, phone, etc.) to trick you into revealing sensitive information or clicking malicious links. In fact, 75% of phishing attacks start with an email.
Social engineering exploits human trust; for example, an email might pretend to be your bank or boss, urging urgent action. Falling for phishing can give attackers your passwords, financial data, or a foothold into a company network.
What To Do?
Make sure you cross-check the email address of every email before clicking on any link. As for text messages and calls, avoid sharing any information or clicking links from unknown numbers that can target you.
2. Malware (Viruses & Trojans)
“Malware” is malicious software designed to harm or hijack systems. This includes viruses, worms, Trojan horses, spyware, and other malicious software. Malware can corrupt files, steal data, or give attackers remote control of your computer.
In fact, virus and malware attacks constitute the single biggest category of cybercrime globally, and 98% of web applications are vulnerable to attacks that can result in malware
What To Do?
Keeping antivirus software updated and only downloading trusted programs are key defenses.
3. Ransomware
Ransomware is a specialized type of malware that encrypts a victim’s data and holds it hostage until a ransom is paid. In recent years, ransomware attacks have exploded – experts call ransomware the fastest-growing cybercrime. These attacks can cripple businesses by locking down critical files. Hospitals, schools, and companies have been extorted for large payouts. Unfortunately, paying a ransom often doesn’t fully restore data and can invite repeat attacks.
What To Do?
Regular data backups and incident response plans are essential to mitigate ransomware threats.
Did You Know, there are four main types of ransomware? These are Magniber, Lockbit, Hive, and BlackCat.
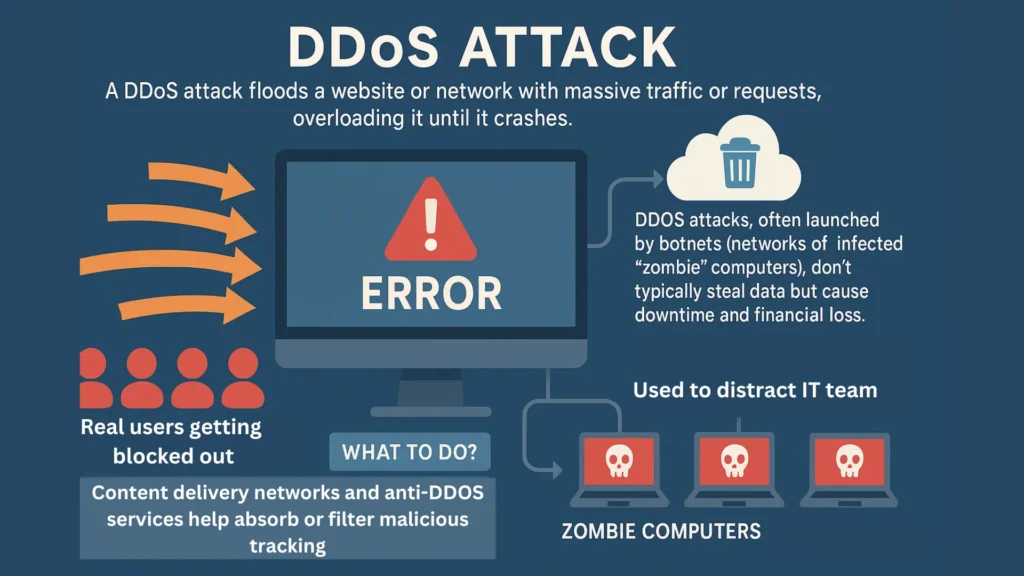
4. Distributed Denial-of-Service (DDoS) Attacks
A DDoS attack floods a website or network with massive traffic or requests, overloading it until it crashes. Imagine countless fake users all trying to access a site at once; this results in real users getting blocked out. DDoS attacks, often launched by botnets (networks of infected “zombie” computers), don’t typically steal data but cause downtime and financial loss. They’ve grown more powerful recently and are sometimes used to distract IT teams while other attacks are attempted.
What To Do?
Content delivery networks and anti-DDoS services help absorb or filter malicious traffic.
5. Password Attacks (Credential Theft)
Weak or stolen passwords are a common security issue in IT. Attackers use methods like brute force (automated guessing of passwords), credential stuffing (trying leaked passwords from one breach on other accounts), or phishing to obtain login credentials. Since many people reuse passwords, a single leak can give hackers access to multiple accounts.
It is estimated that nearly 75% people don’t follow best practices for passwords, which is the leading cause of such breaches.
What To Do?
Using strong, unique passwords and enabling multi-factor authentication can thwart most of these attacks (more on protection later).
6. Insider Threats
Not all threats come from outside hackers. Insiders, like employees or contractors, can also cause breaches. Insider threats may be malicious (a disgruntled worker stealing data) or accidental (an employee falling for a scam or misconfiguring a system). Studies show the human element is involved in the vast majority of breaches. In fact, 95% of all data breaches involve some kind of human error or misuse.
What To Do?
Regular staff training, access controls (ensuring people only access what they truly need), and monitoring can help reduce insider risks.
7. Unpatched Software and Zero-Day Exploits
When software (like an operating system, database, or application) has a security flaw, attackers can exploit it to gain unauthorized access, and this is often called an exploit. If the vulnerability is known, developers release security patches to fix it.
But if systems aren’t kept updated with patches, they remain susceptible. Worse, if attackers discover a new vulnerability before it’s publicly known or fixed (a so-called zero-day exploit), they can attack with impunity.
What To Do?
Update your software regularly and apply patches promptly to close known security holes. Also, ensure that your organization is using reputable software like Windows and macOS.
8. Man-in-the-Middle (MitM) Attacks
In a MitM attack, a hacker secretly intercepts and possibly alters the communication between two parties. For example, on a public Wi-Fi, an attacker could eavesdrop on data you send to a website or insert malicious code. They effectively “sit in the middle” of your connection. This can lead to theft of login credentials, credit card numbers, or session hijacking.
What To Do?
Using encrypted connections (HTTPS, VPNs) and avoiding sensitive transactions on public networks helps guard against MitM eavesdropping.
9. SQL Injection and Web Application Attacks
Many websites rely on databases (often using SQL). Attackers can use SQL injection by inputting malicious code into a vulnerable form or URL, tricking the website into revealing data or giving unauthorized access. Similarly, attacks like Cross-Site Scripting (XSS) inject malicious scripts into websites that then run in other users’ browsers. These kinds of web application attacks can steal data, deface sites, or distribute malware.
What To Do?
Secure coding practices, web application firewalls, and input validation are defenses developers implement to prevent these exploits.
10. Supply Chain Attacks
A supply chain attack targets not you directly, but one of your trusted partners or software providers as a backdoor into your system. For example, hackers might compromise a popular software update (as happened in the infamous SolarWinds incident) so that when thousands of businesses install the update, the malware comes bundled with it. Similarly, attackers might breach a smaller vendor that has network access to a bigger target. Supply chain attacks are especially insidious because they undermine the trust of normal operations.
What To Do?
Vetting third-party vendors, using digital code signatures, and monitoring for unusual network activity can help mitigate this threat.
11. Internet of Things (IoT) Attacks
IoT devices often have lax security (default passwords, infrequent updates), making them easy targets. Attackers can hijack IoT gadgets to spy, i.e., hack a webcam, steal data from a smart sensor, or recruit them into botnets for DDoS attacks.
What To Do?
It’s critical to change default credentials on smart devices, apply updates, and isolate them on separate networks when possible.
12. Advanced Persistent Threats (APTs)
An APT is when a highly skilled attacker (often a state-sponsored group) gains unauthorized access to a network and stays undetected for a long period, stealing data or surveilling. APT actors often use a combination of techniques (phishing for initial entry, malware, zero-days, etc.) and stealthy tactics to maintain persistence.
Their targets are typically strategic, including governments, research labs, critical infrastructure, or corporations with valuable intellectual property. While APTs may not directly target average users, these threats represent the most sophisticated end of attacks and drive many defensive innovations.
What To Do?
Robust network monitoring, threat intelligence, and incident response planning are crucial for effectively dealing with APTs.
4 Emerging Cybersecurity Threats and Challenges
Much like how technology evolves rapidly, so do cybercriminals, unfortunately. Here are 4 emerging IT security threats and challenges that are on the rise and expected to shape the cybersecurity landscape in 2025 and ahead:
While generative AI is tremendously beneficial, it can also craft highly convincing phishing emails or even code malware, at scale and with minimal effort. Even more unsettling is the rise of deepfake fraud, which uses AI to create fake but realistic voices, images, or videos.
Scammers have begun cloning the voices of CEOs or loved ones to trick people into transferring money, and this type of scam is increasing rapidly. In fact, in the past 3 years, DeepFake fraud attempts have increased by 2137%.
What To Do?
Staying skeptical of unusual requests (even if “heard” or “seen” via video) and using verification steps (call the person back on a known number, for instance) are crucial defenses. The cybersecurity community is also developing deepfake detection tools to combat this threat.
2. Supply Chain and Third-Party Software Attacks
As mentioned earlier, supply chain attacks are a major concern, and they’re becoming more frequent. Modern organizations rely on a complex web of software and vendors. Each link is a possible weak point. We’ve seen attackers target software updates, open-source libraries, and even security products themselves to distribute malware widely.
What To Do?
Mitigating this requires careful vendor security assessments, network segmentation (so a breach in one partner’s connection doesn’t compromise everything), and keeping an eye on the integrity of software components through techniques like checksums or SBOMs (Software Bill of Materials).
3. Cloud Security Challenges and Remote Work Risks
The shift to cloud computing and remote work has expanded the attack surface. More data and applications now reside in cloud services, which, if misconfigured, can be left exposed to the internet. In recent years, there have been many incidents of databases or storage buckets inadvertently left unsecured, leaking millions of records. Additionally, remote work means more reliance on home networks and personal devices, which may not be as secure as corporate networks.
What To Do?
To counter this, companies are adopting Zero Trust security (never assume an environment is secure, always verify users and devices) and improving cloud configuration monitoring. Individuals should ensure their home Wi-Fi is secured, use VPNs when appropriate, and follow company security guidelines for remote access.
4. Quantum Computing Threat to Encryption
Within the next decade or so, a powerful quantum computer could potentially break commonly used encryption (like RSA or ECC) that protects data and communications.
This threat isn’t here yet, but post-quantum cryptography is an emerging field working on new encryption methods that would resist quantum attacks.
What To Do?
Organizations, especially those dealing with long-lived sensitive data (like state secrets, health records), are starting to plan for a transition to quantum-safe encryption in the coming years. But whether or not it is a viable strategy, only the future will tell.
Who Is Most Vulnerable to Cyber Attacks? (Targets and Victims)
With such different types of malicious cyber attacks, it is natural to ask the question, “Who do cyber attackers most often go after?”
Well, the answer is… Everyone.
However, some groups are especially attractive targets due to higher potential payoff or weaker defenses:
- High-Value Industries: Sectors that hold especially valuable data tend to be prime targets, like financial services and healthcare industries.
- Small and Medium Businesses (SMBs): It’s a common misconception that only big companies get hacked, but small businesses are equally targeted, if not more. In fact, in 2019, 43% of cyber breaches targeted small businesses.
- Individuals (You and Me): Cybercriminals often attack individuals to steal personal data, account logins, or banking information. Unfortunately, older adults have become frequent victims of online fraud.
- Specific Roles or Personnel: Within organizations, attackers often target certain roles. For example, executives and finance staff are prime targets for business email compromise (BEC) scams and spear-phishing. An attacker might impersonate a CEO or CFO (even using a deepfake voice as discussed) to trick an employee in accounting into wiring money.
How to Protect Against Cyber Threats: Essential Best Practices
Strengthening your cyber defenses doesn’t have to be complicated. Focus on these fundamental steps to protect yourself and your organization:
1. Use Strong Passwords & Multi-Factor Authentication (MFA)
- Choose unique, complex passwords for each account.
- Whenever possible, enable MFA, which requires a second form of verification.
- MFA can reduce your risk of account compromise by 99%.
2. Be Cautious With Emails & Links
- Don’t trust unexpected emails, especially those requesting sensitive information or urgent action.
- Verify sender addresses, and avoid clicking links or downloading attachments unless sure of the source.
- When uncertain, confirm the request through another method.
3. Keep Software Up to Date
- Regularly update your operating system, browser, and all apps.
- Enable automatic updates to quickly patch vulnerabilities.
4. Regularly Back Up Your Data
- Frequently back up important files, using offline storage or a secure cloud solution
- Maintain some backups offline, so they can’t be encrypted by ransomware.
5. Use Security Software & Firewalls
- Run up-to-date antivirus or anti-malware software.
- Enable firewalls to block suspicious network traffic.
- Businesses should consider advanced protections like next-generation firewalls and intrusion detection systems.
6. Secure Your Networks & Use Encryption
- Protect Wi-Fi with a strong password and WPA2/WPA3 encryption.
- Avoid public Wi-Fi for sensitive actions unless using a VPN.
- Encrypt sensitive data both in transit (e.g., HTTPS, VPN) and at rest (e.g., full-disk encryption).
7. Limit Access & Apply Zero Trust Principles
- Give users only the permissions they need for their role.
- Segregate networks and resources to minimize the impact of a breach.
- Employ “Zero Trust” strategies, where every connection requires verification.
8. Educate & Train Regularly
- Participate in ongoing cybersecurity training to recognize threats like phishing.
- Stay informed about new tactics used by cybercriminals.
- Well-trained users and staff are much less likely to fall victim to common attacks.
The CCI Training Computer & Network Administrator Program provides you with an understanding of IT security issues.
NOTE: If you want to understand the mindset of how a hacker thinks and be better prepared for cyber attacks, we highly recommend workshops like Certified Ethical Hacking (CEH).
Final Words
Whether we like it or not, cyber threats in the IT industry will continue to evolve, but with awareness and vigilance, we can all do our part to counter them. You need to be extra careful if you work on a help desk, as an IT support, or as a network administrator, or in information security, as you need to be able to diagnose and treat all of the problems outlined above.
With that said, cybersecurity is a team effort that requires individuals to practice smart security habits and organizations to implement protective measures. By understanding the threats and following best practices, you become a much tougher target, and you contribute to a safer digital community overall.
Program Offered
- Pharmacy Technician Training
- Online Medical Assistant
- Medical Billing and Coding Specialist Program
- Cloud Computing Technician Training
- Computer Network Technician
- Business and Accounting
- Radiology Technician Training
- Medical Assistant Program
- Computer Support Technician
- Cybersecurity Program
- Virtual Assistant Training

This article is written by
Share this article
Program Offered
- Pharmacy Technician Training
- Online Medical Assistant
- Medical Billing and Coding Specialist Program
- Cloud Computing Technician Training
- Computer Network Technician
- Business and Accounting
- Radiology Technician Training
- Medical Assistant Program
- Computer Support Technician
- Cybersecurity Program
- Virtual Assistant Training

This article is written by
Share this article
Frequently Asked Questions FAQ's
What are the top 5 major threats to cybersecurity?
These are the top 5 major cyber threats:
- Phishing
- Malware (including ransomware)
- Password attacks/credential theft
- Insider threats
- Distributed Denial-of-Service (DDoS) attacks
What is 90% of cyber attacks?
While not 90%, according to statistics, 75% of all cyber attacks are phishing attacks.
What are the top 5 emerging cybersecurity challenges?
- AI-driven attacks (deepfakes, generative AI)
- Supply chain & third-party software attacks
- Cloud security and remote work vulnerabilities
- Quantum computing threats to encryption
- Rise in IoT threats
Who do most cyber criminals target?
Mostly, high-value industries (finance, healthcare), SMBs, and older individuals who are not tech-savvy.
What industry gets the most cyber attacks?
Finance and healthcare industries are extremely prone to cyber attacks due to high rewards, such as sensitive information access.
How do most cyber attacks begin?
Most cyber attacks start with an email with tempered links.
What is the fastest-growing cybercrime in the world?
Ransomware is the fastest-growing form of cyber threat in the world as of 2025.
Is it worth getting into cybersecurity?
Absolutely! With such a rise in cyberattacks, the IT professionals vetted in cybersecurity are in high demand.
Related Articles