A call by John Oliver on May 7 resulted in the shutdown of the Federal Communication Commission’s (FCC), while tens of thousands of computer systems were at a standstill after a global ransomware attack began on May 12. Finally, Disney announced on May 15 that one of their movies had been stolen and held for ransom.
Together, these represent the vast array of cyber threats that businesses of all kinds, and the IT professionals that work with them, need to be aware of to prevent disaster.
What is Denial of Service (DoS)?
A DoS attack involves lots of different computers attempting to use a single website at one time. The dramatic increase of data is too much, and the system shuts down.
Not only people aiming to register their comments but others with more malicious intent bombarded the site with information, and the influx of traffic proved to be more than the website’s servers could handle.
On his show Last Week Tonight, John Oliver called for viewers to register their comments in protest of the FCC’s attempts to repeal their 2015 net neutrality ruling. However, the website also became the target of a DoS attack.
Occasionally, DoS can be self inflicted. When the Australian National Census went digital, people across the nation were asked to log onto an online form at the same designated time. This huge increase in traffic, although expected, brought the Census website to a standstill. Obviously, this example of DoS should have been prepared for and avoided by a pro-active IT department.
How can the IT department avoid DoS situations?
- Monitor analytics: Monitor your website’s analytics so you can identify and respond to spikes in traffic.
- Keep up-to-date: This should go without saying, but make sure you keep your security and software systems up-to-date to prevent and limit the effects of a cyber attack.
- Plan in advance: The only way to know how you will deal with any of the cyber attacks in this list is to make a plan beforehand. Knowing how to prevent a DoS attack and the consequences of every scenario takes time and resources.
Article continues after recommendations
Recommended for you
-
Cloud Computing Technician Training
The “cloud” refers to resources hosted in a data center that you access over the internet. Rather than keeping data or operating applications on your own computer or in-house server.
-
Computer Network Administration
IT security refers to the measures taken to protect digital systems, networks, and information from theft, harm, or unauthorized interference.
What is Malware?
Malware is software that attacks from within your computer once activated. Ransomware, which we discussed earlier, is a subset of malware that requires the computer owner to pay money before their data is released. The malware itself doesn’t require a ransom to fix and can include a variety of worms, Trojans, and viruses.
The recent WannaCrypt ransomware was a global attack with over 50,000 systems hit and counting. Again, the healthcare sector took the brunt of the attack with potentially devastating effects, as it attacks the ability to access the data so vital for timely medical aid.
The solution? Accidental in fact. Researchers had discovered the malware was reaching out to a certain domain to activate. In order to record the ransomware’s activity, researchers registered the domain it was contacting. Serendipitously, they had found the WannaCrypt kill switch.
What can you do about ransomware attacks?
- Upgrade your system: WannaCrypt took advantage of a hole in in Windows XP’s security, a system that is now 15 years old. A patch was released for the outdated system after the attack; two months after more recent versions received the same fix.
- Install appropriate systems: Ensure you have the best and most up-to-date antivirus and firewall software to warn you of suspicious files.
- Create a culture of awareness: Teach staff how to identify and avoid suspicious content in emails and downloads. Research has shown that despite receiving cyber security training, 24% of employees would use unsafe practices to complete the task at hand.
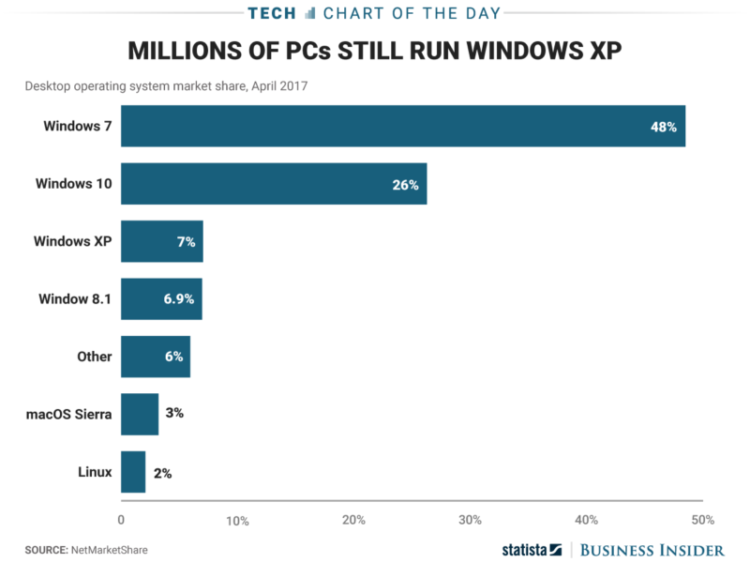 IMAGE: Business Insider (https://www.businessinsider.com.au/how-many-people-use-windows-xp-chart-2017-5/)
IMAGE: Business Insider (https://www.businessinsider.com.au/how-many-people-use-windows-xp-chart-2017-5/)Hacking: inside and out
Data can be stolen by people both within and outside of a company. While the theft of Disney’s unnamed movie is likely to be the result of external hackers, the risk from company employees is just as great.
Following the leaking of Orange Is the New Black when Netflix didn’t pay up, it has been reported that the next installment of Pirates of Caribbean may be the victim of the Disney ransom. Disney is working with investigators and will not pay the ransom. The hackers have said that if the bitcoin ransom is not paid, they will release the film in 20-minute installments.
How can you reduce the risk of hacking?
- Change passwords: Ensure passwords are changed regularly, and that strong passwords that include numbers, symbols and uppercase letters are used.
- Revoke access: When a person leaves the company, regardless of the feeling between parties, always revokes access to company information.
- Pay the ransom: While some may argue paying the ransom encourages bad behavior, when the data being ransomed is vital to someone’s survival it’s hard to avoid.
These cyber attacks serve as an important reminder to those seeking any IT role. You leave your company vulnerable to attack if you do not keep systems updated. The threats faced by those reliant on the internet (which is pretty much everyone) are constantly evolving, and to work in IT, you need to stay abreast of these changes.
Request More Information About CCI Training Center Now.
The best way to decide on a school is to ask for more information. Even though you can review available courses online, submitting a request for more information or speaking with a counselor can help you decide if the school and program are right for you. Are you ready to kickstart your new career and find nearby job training? Give CCI Training Center a call at 1-972-895-7055 now.